
There is a lot of confusion between vulnerability assessments and penetration testing. Some think they’re the same while others wonder which solution is better. We’ll discuss what these terms mean and how they are different. We’ll also discuss how tools can help you with this process and why you might want to use them. Finally, we will list the six best tools for vulnerability assessment and penetration testing.
Defining terms:
1. Vulnerability assessment
It is an evaluation to determine areas of weakness and possible attacks on a network or computer system. The goal is to identify any vulnerable network assets before hackers do. This information can then be used by an IT personnel to make necessary changes that will improve security and prevent a breach from occurring in the future. Vulnerability assessments are often done with tools as they provide valuable insights into potentially vulnerable targets over large networks or systems.
How is it different from a penetration test?
Vulnerability assessments are less invasive than penetration testing which makes them more appropriate for some situations such as when you have limited time or resources, cannot shut down operations during the test, etc. However, unlike penetration tests, vulnerability assessments do not attempt to exploit the vulnerabilities they find.
Next, we will discuss penetration testing.
2. Penetration testing
This type of assessment (or test) attempts to exploit weaknesses and possible attacks on networks and computer systems by actually trying to gain access or break into them using various methods. These tests reveal which attack vectors are most effective against specific targets so that IT personnel can prioritise their efforts for making necessary changes before hackers do it for them. Penetration tests may also identify additional ways that attackers could penetrate defences beyond those initially identified via vulnerability assessments, especially if they have already been applied. While this sounds more intrusive and risky, a well-planned penetration test can be very helpful in increasing the overall security posture.
How is it different from a vulnerability assessment?
Penetration testing is more invasive than vulnerability assessments as it typically requires access to the systems being tested. It can also be more disruptive if done on live systems. However, because penetration tests attempt to exploit vulnerabilities, they are often more revealing about an organisation’s true security posture. As such, they are generally seen as a better indicator of risk than vulnerability assessments.
Which is better?
This depends on what your security goals are. If you want a broad overview of your system’s vulnerabilities then a vulnerability assessment is likely the better choice. If you want to find out which attack vectors are most effective at compromising your systems, then penetration testing is likely the better choice.
Why use tools?
The main reason is that:
- using a tool will allow you to scan and test a much larger network or system in less time
- when used properly, these tools can provide valuable insights into potential vulnerabilities
- so IT personnel have time to react before hackers do it for them.
This means using tools for vulnerability assessment or penetration testing can be very helpful if done correctly but also dangerous if not done correctly:
- as they may reveal sensitive information about an organisation’s defences and weaknesses
- expose more risks than were intended by the test
- result in unauthorised access to systems or data
Therefore, it is important that when using tools for vulnerability assessment or penetration testing, you use them in conjunction with professional advice and guidance.
6 best vulnerability assessment and penetration testing tools
Tools for Vulnerability Assessment:
This tool provides detailed reports on vulnerabilities found across a network or website as well as suggested remediation actions. It can be used to evaluate:
- websites, mobile apps and APIs
- network vulnerabilities (on-premises or in the cloud)
- infrastructure configuration (e.g., operating systems, network devices, etc.)
- Nessus Professional
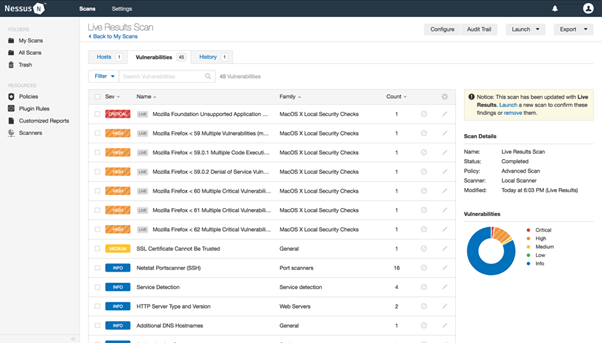
This tool is known for its ease of use as well as for being able to scan large networks quickly. It provides detailed reports on each asset being tested that include information about how severe each vulnerability may be, along with suggested remediation actions.
- Nmap
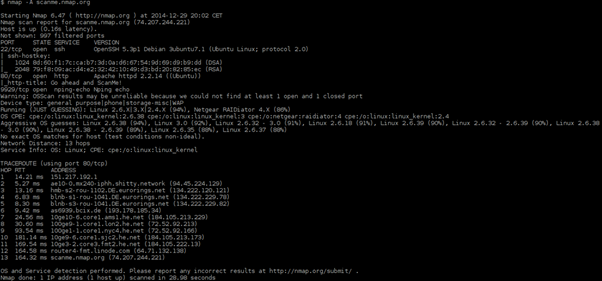
This tool is free to use, open source and can scan for a lot of things, including:
- open ports
- OS version and details
- network vulnerabilities
These are just a few examples of the many tools available for assessing vulnerabilities. Using these or other similar tools may not be the only thing that is needed to get a full picture of vulnerabilities in your network or system, but they can provide valuable information about what areas need improvement.
Tools for Penetration Testing:
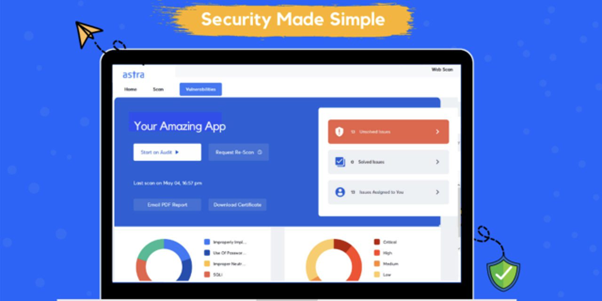
- Astra Pentest – This tool allows you to test the effectiveness of your security policies and procedures by simulating attacks on your network or website. It will provide information about how well protected you are against such threats as:
- malware
- ransomware
- phishing emails, etc.
- Metasploit
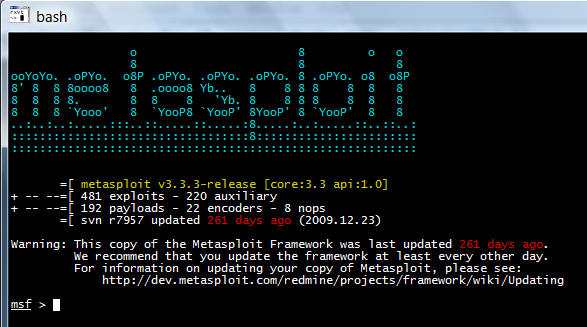
This tool is used to test exploits in a controlled environment. It allows you to generate payloads and exploit codes for specific operating systems.
- Sqlmap
This tool will allow users to exploit SQL injection vulnerabilities on websites or web applications. It works by sending malicious requests that causes the system under attack to return sensitive data from its database(s) back to an attacker’s computer.
Using these or other similar tools may not be the only thing that is needed to get a full picture of vulnerabilities in your network or system, but they can provide valuable information about what areas need improvement.
Conclusion
It is important to remember that no matter how good your antivirus software may be, it will never stop all attacks from happening. The best way to protect yourself against malicious hackers and cybercriminals is through education, awareness training programs, and regular vulnerability assessments / penetration tests by qualified professionals who can identify potential weaknesses before anything bad happens.
